In the general case, a firewall (aka firewall) is a specialized hardware and software complex that minimizes the possibility of harmful external influences on the network section entrusted to it.
Of course, more reliable protection provide firewalls in separate modules, which are usually located in the server room and are very solid equipment.
However, such complexes cost several thousand dollars and "mere mortals" (including most of the system administrators) get along ready-made software solutions such as the Windows 7 firewall.
Essentially, a firewall acts as a checkpoint at or where it is installed.
Which package to skip and which one to block Brandmauer determines with the help of the rules laid down in it in advance. These rules vary depending on the software version, and users can customize their rules in the process.
The need to create your own rules for the firewall arises provided that the firewall is enabled, but special permissions are required for some programs (primarily for incoming traffic). Outgoing traffic restrictions may also be imposed.
The technique of working with an onboard firewall does not change much from version to version of Windows. So…
How to enable Windows 7 firewall.
Let's consider how to independently connect and configure the internal firewall
1. How to enter windows 7 firewall?
Click on the "Start" button and select "Control Panel" from the program menu on the right.
After that, the Control Panel window will appear, where you should select "Windows Firewall"
The firewall settings window will appear. If the firewall is disabled, it will look something like this.
On the right is a list of settings and networks that are currently active.
On the left, you can see the options for configuring the firewall.
2. How to start windows 7 firewall?
In order to turn on the firewall, select the "Turn on and off Windows Firewall».

In the next window, select "Enable ..." to desired networks and set the appropriate markers, then press "Enter" (or soft button"OK").
3. Where is the firewall on windows 7?
If the Firewall was accidentally disabled and the security alert settings have not been changed, then it can be much easier to find. A checkbox will appear in the desktop panel on the right, clicking on which will open a menu of the following type:
V in this case to enable the firewall, just select the appropriate item.
Now your firewall on windows 7 is enabled and the settings window looks like this:

 Howconfigure windows 7 firewall?
Howconfigure windows 7 firewall?
Configuring a firewall on Windows 7 consists in prescribing appropriate rules for it.
It is advisable, immediately after enabling the firewall, to register an exclusion rule for.
How to add a program to windows 7 firewall exceptions?
To do this, select the first item of the left menu - "Allow the program to start ...", after which the settings window will appear:


In the following list you should find the necessary program that you want to add to windows 7 firewall exceptions. In this case, it is MsSE, which is free antivirus and within the framework does an excellent job of its duties.

If necessary, check or uncheck the corresponding lines and click OK.
The window will appear again general settings Firewall.
To fine-tune the firewall on Windows 7, select the "Advanced options" menu item, where all the rules for all connections are thoroughly spelled out. It is not recommended to configure advanced parameters without proper experience. In this area, you can manually register rules.
Let's consider an example:

In the right column, select Outbound Rules.
All available rules for incoming connections will be displayed in the middle column.
In the left column, find the item "create a rule" and click on it.
The rule settings window will appear.

On the left are the “steps” that need to be taken, on the right are the settings options.
To configure the rules for a specific program, click "next".
In the next window, you will need to select the required program, if the rule does not apply to all applications installed on the computer.
In the "actions" window, you should inform whether we allow or deny the connection in this rule, as well as configure additional conditions (encryption, encapsulation).
The next step "Profile" determines under which network profile this rule will work.
The last step is the Name.
Click on the "Finish" button and the new rule will be added to the firewall settings on your computer.
Published on March 10, 2009 by No CommentsOS Management Console (MMC) Snap-in Windows Vista™ is a network-logging firewall for workstations that filters incoming and outgoing connections according to given settings... You can now configure your firewall and IPsec settings using a single snap-in. This article describes how Windows Firewall works in increased security, typical problems and solutions.
How Windows Firewall with Advanced Security works
Windows Firewall with Advanced Security is a network-logging firewall for workstations. Unlike router firewalls, which are deployed at a gateway between a local network and the Internet, Windows Firewall is designed to run on separate computers. It only monitors traffic on the workstation: traffic coming to the IP address of this computer, and outgoing traffic from the computer itself. Windows Firewall with Advanced Security performs the following basic operations:
- The incoming packet is checked and compared with the list of allowed traffic. If the packet matches one of the list values, Windows Firewall forwards the packet to TCP / IP for further processing. If a packet does not match any of the list values, Windows Firewall blocks the packet and, if logging is enabled, creates an entry in the log file.
The list of allowed traffic is formed in two ways:
- When a connection controlled by Windows Firewall with Advanced Security sends a packet, the firewall creates a value in the list to allow return traffic. Additional permission is required for the corresponding inbound traffic.
- When you create an Allow Windows Firewall with Advanced Security rule, traffic for which the rule is created will be allowed on the computer that is running Windows Firewall. This computer will accept explicitly allowed inbound traffic in server modes, client computer or a node of a peer-to-peer network.
The first step in troubleshooting Windows Firewall issues is to check which profile is active. Windows Firewall with Advanced Security is an application that monitors your network environment. The Windows Firewall profile changes when the network environment changes. A profile is a set of settings and rules that are applied depending on the network environment and current network connections.
The firewall distinguishes between three types of network environments: domain, public and private networks. A domain is a network environment in which connections are authenticated to a domain controller. By default, all other types of network connections are treated as public networks. When a new one is found Windows connections Vista prompts the user to indicate if this network private or public. The general profile is intended for use in public places such as airports or cafes. The private profile is intended for use at home or in the office, or on a secure network. To define a network as private, the user must have the appropriate administrative authority.
Although the computer can be connected to networks at the same time different types, only one profile can be active. The choice of an active profile depends on the following reasons:
- If all interfaces use domain controller authentication, the domain profile is used.
- If at least one of the interfaces is connected to a private network and all the others are connected to the domain or private networks, the private profile is used.
- In all other cases, the general profile is used.
Click the node to define the active profile Observation in snap Windows Firewall with Advanced Security... Above the text Firewall status it will indicate which profile is active. For example, if a domain profile is active, the following text will be displayed at the top Domain profile is active.
With profiles, Windows Firewall can automatically allow inbound traffic for special computer management tools when the computer is in a domain, and block the same traffic when the computer is connected to a public or private network. Thus, defining the type of network environment protects your local network without compromising the safety of mobile users.
Common problems with Windows Firewall with Advanced Security
The following are the main issues with Windows Firewall with Advanced Security:
- Traffic is rejected by Windows Firewall
- Computer does not respond to ping requests
- Impossible to get general access to files and printers
- Impossible remote administration Windows firewall
In the event that traffic is being blocked, you should first check if the firewall is enabled and which profile is active. If any of the applications are blocked, make sure that in the snap-in Windows Firewall with Advanced Security there is an active allow rule for the current profile. Double-click the node to verify that an Allowing rule exists. Observation and then select a section Firewall... If there are no active permissive rules for this application, go to the node and create a new rule for this application. Create a rule for a program or service, or specify a rule group that applies to this function, and make sure that all rules for this group are enabled.
To verify that an Allowing Rule is not overridden by a Blocking Rule, follow these steps:
- In a snap tree Windows Firewall with Advanced Security click node Observation and then select a section Firewall.
- View a list of all active local and group policy rules. Deny rules override permissive rules even if the latter are more precisely defined.
Group Policy prevents local rules from being applied
If Windows Firewall with Advanced Security is configured using group policy, the administrator can specify whether to use firewall rules or connection security rules created by local administrators. This makes sense if there are configured local firewall rules or connection security rules that are not in the corresponding section of the settings.
To find out why local firewall rules or connection security rules are missing from the Monitoring section, follow these steps:
- In snap Windows Firewall with Advanced Security, click the link Windows Firewall Properties.
- Select the active profile tab.
- In chapter Parameters, press the button Tune.
- If local rules apply, section Combining rules will be active.
Rules requiring secure connections can block traffic
When creating a firewall rule for inbound or outbound traffic, one of the options is. If selected this function, you must have an appropriate connection security rule or a separate IPSec policy that determines which traffic is protected. Otherwise, this traffic is blocked.
To check that one or more rules for an application require secure connections, follow these steps:
- In a snap tree Windows Firewall with Advanced Security click the section Inbound rules... Select the rule you want to check and click on the link Properties in the scope of the console.
- Select a tab Are common and check if the selected value of the radio button is Allow only secure connections .
- If the parameter is specified for the rule Allow only secure connections, expand the section Observation in the snap-in tree and select the section. Make sure that the appropriate connection security rules exist for the traffic defined in the firewall rule.
Warning:
If you have an active IPSec policy, make sure that the policy is protecting the traffic you need. Do not create connection security rules to avoid conflicting IPSec policy and connection security rules.
Unable to allow outgoing connections
- In a snap tree Windows Firewall with Advanced Security Choose a section Observation... Select the active profile tab and under Firewall status check that outgoing connections that do not fit the Allow Rule are allowed.
- In chapter Observation Choose a section Firewall to make sure that the required outbound connections are not specified in the deny rules.
Mixed policies can block traffic
You can configure firewall and IPSec settings using various Windows interfaces.
Creating policies in multiple locations can lead to conflicts and blocking traffic. The following setting points are available:
- Windows Firewall with Advanced Security. This policy is configured using the appropriate snap-in locally or as part of Group Policy. This policy controls the firewall and IPSec settings on computers running Windows Vista.
- Windows Firewall Administrative Template. This policy is configured using the Group Policy Object Editor in the section. This interface contains Windows Firewall options that were available before the emergence of Windows Vista, and is designed to configure the GPO that controls previous versions Windows. Although these parameters can be used for computers under Windows control Vista, it is recommended to use the policy instead Windows Firewall with Advanced Security because it provides more flexibility and security. Note that some of the domain profile settings are common to the Windows Firewall Administrative Template and Policy Windows Firewall with Advanced Security, so you can see here the parameters configured in the domain profile using the snap-in Windows Firewall with Advanced Security.
- IPSec policies. This policy is configured using the local snap-in IPSec Policy Management or the Group Policy Object Editor under Computer Configuration \ Windows Configuration \ Security Settings \ IP Security Policies on Local Computer. This policy defines the IPSec settings that can be used by both previous versions of Windows and Windows Vista. Do not apply this policy and the connection security rules defined in the policy at the same time on the same computer Windows Firewall with Advanced Security.
To view all these settings in the corresponding snap-ins, create your own snap-in for the management console and add snap-ins to it Windows Firewall with Advanced Security, and IP security.
To create your own Management Console snap-in, follow these steps:
- Click the button Start, go to the menu All programs, then in the menu Standard and select the item Execute.
- In a text box Open type mmc and press key ENTER.
- Continue.
- On the menu Console select an item.
- In the list Available rigs select rig Windows Firewall with Advanced Security and press the button Add.
- Click the button OK.
- Repeat steps 1 through 6 to add snap Control group policy and IP Security Monitor.
- Save the console for future use before closing the snap-in.
Use the following procedure to check which policies are active on the active profile:
To check which policies are being applied, follow these steps:
- At the command line, enter mmc and press ENTER.
- If a User Account Control dialog box appears, confirm the requested action and click Continue.
- On the menu Console select item Add or remove snap-in.
- In the list Available rigs select rig Group Policy Management and press the button Add.
- Click the button OK.
- Expand a node in a tree (usually the forest tree in which the this computer) and double-click the section in the details pane of the console.
- In the action area, click the link Additional actions and select the command Resultant set of policy wizard.
- Click the button Further... Set the radio button to value This computer or Another computer(enter computer name or click Overview). Press the button again Further.
- Select switch value Display policy settings for of meanings current user or another user... If you do not want to display the policy settings for users, but only the policy settings for the computer, select the value of the radio button Do not display user policy (view only computer policy) and press the button twice Further.
- Click the button Ready... The Group Policy Results Wizard generates a report in the details pane of the console. The report contains tabs Summary, Parameters and Policy events.
- To check that there is no conflict with IP security policies, after generating the report, select the tab Parameters and open Computer Configuration \ Windows Configuration \ Security Settings \ IP Security Settings in Directory Service Active Directory... If the last section is missing, then no IP security policy has been set. Otherwise, the name and description of the policy and the GPO to which it belongs will be displayed. When IP Security policy and Windows Firewall with Advanced Security policy are used concurrently with connection security rules, these policies may conflict. We recommend that you use only one of these policies. The best solution is to use IP security policies in conjunction with Windows Firewall with Advanced Security rules for inbound or outbound traffic. Difficult policy conflicts can arise if the settings are configured in different places and are not consistent with each other.
- Expand the section to view the settings defined in the Windows Firewall Administrative Template. Computer Configuration \ Administrative Templates \ Network \ Network Connections \ Windows Firewall.
- To view the latest events related to the current policy, you can go to the tab Policy Events in the same console.
- To view the policy used by Windows Firewall with Advanced Security, open a snap-in on the diagnosed computer and view the settings under Observation.
There can also be conflicts between policies defined in local GPOs and scripts configured by the IT department. Verify all IP security policies using IP Security Monitor or by typing the following command at a command prompt:
netsh IPsec dynamic show all
To view administrative templates, open the snap-in Group policy and in the section Group Policy Results review if there are settings that are inherited from Group Policy that might cause traffic to be denied.
Open the IP Security Monitor snap-in to view the IP Security Policies. Select the local computer in the tree. In the console scope, select the link Active politics , Basic Mode or Fast mode... Check for competing policies that might block traffic.
In chapter Observation snap Windows Firewall with Advanced Security You can view existing rules for both local and group policy. For getting additional information refer to the section " Using the Observation Function in a Snap Windows Firewall with Advanced Security »Of this document.
To stop the IPSec Policy Agent, follow these steps:
- Click the button Start and select a section Control Panel.
- Click the icon System and its maintenance and select a section Administration.
- Double click the icon Services... If a User Account Control dialog box appears, enter the required user details with the appropriate authority and click Continue.
- Find the service in the list IPSec Policy Agent and make sure it has the status "Working".
- If the service IPSec agent launched, click on it right click mouse and select the item Stop... You can also stop the service IPSec agent from the command line using the command
Peer-to-peer policy can cause traffic to be denied
For connections using IPSec, both computers must have compatible IP security policies. These policies can be defined by using the Windows Firewall Connection Security Rules snap-in IP security or another IP security vendor.
To check IP security policy settings on a peer-to-peer network, follow these steps:
- In snap Windows Firewall with Advanced Security select node Observation and Connection security rules to ensure that both hosts are configured with IP security policy.
- If one of the computers in the peer-to-peer network is running more than early version Windows than Windows Vista, make sure that at least one of the native mode cipher suites and one of the fast mode cipher suites use algorithms that are supported by both nodes.
- Click a section Basic Mode, in the details pane of the console, select the connection to test, then click the link Properties in the scope of the console. Review the connection properties for both nodes to ensure they are compatible.
- Repeat step 2.1 for the section Fast mode... Review the connection properties for both nodes to ensure they are compatible.
- If you are using Kerberos version 5 authentication, make sure the host is in the same or trusted domain.
- If you are using certificates, make sure the required check boxes are selected. Certificates using Internet Key Exchange (IKE) require digital signature... Certificates using Authenticated IP (AuthIP) require client authentication (depending on the server authentication type). For more information on AuthIP certificates refer to the article Authenticated IP in Windows Vista AuthIP in Windows Vista at the Microsoft website.
Unable to configure Windows Firewall with Advanced Security
Windows Firewall with Advanced Security settings are unavailable (dimmed) in the following cases:
- The computer is connected to a centrally managed network, and the network administrator uses Group Policies to configure Windows Firewall with Advanced Security settings. In this case, at the top of the snap Windows Firewall with Advanced Security You will see the message "Some settings are controlled by Group Policy." Your network administrator configures the policy, thereby making it impossible for you to change the Windows Firewall settings.
- The Windows Vista computer is not connected to a centrally managed network, but Windows Firewall settings are controlled by local Group Policy.
To change Windows Firewall with Advanced Security settings by using Local Group Policy, use the snap-in Politics local computer ... To open this snap, in
The control panel contains all the necessary items to set up your computer. We will now consider in more detail one of these components.
What is Windows Firewall?

How Windows Firewall works.
Step 1 ... We launch the control panel. To do this, press the menu Start and chooseControl Panel.
Here we select an itemsystem and safety.

Step 2
... In order to go to the settings, in the window that appears, go to the section Windows firewall by clicking on it once.
Step 3
... If you already have another anti-virus software installed on your computer software then I recommenddisable windows firewall.If, on the contrary, you have not yet had time to install antivirus program then I recommend a firewall turn on , this will protect your computer from viruses.
But you still need to use the recommended protection settings. To enable these parameters, click on the item.

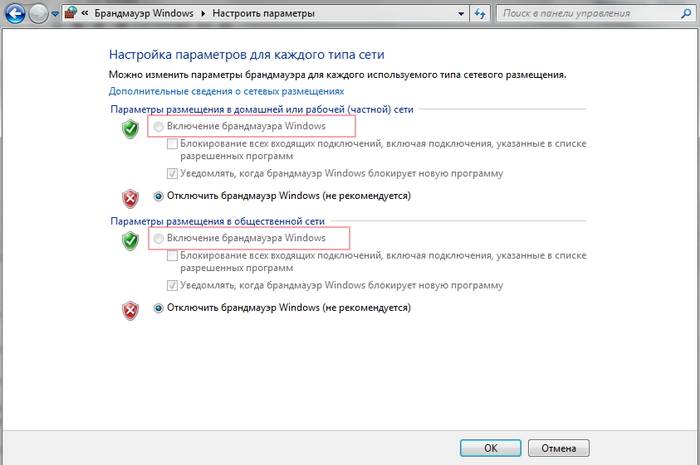
Step 4 ... In a new window in the block Hosting options on your home or work (private) network put the switch on the Enable Windows Firewall field.
In the same part, you can Mark ticked items:- Block all incoming connections, including connections specified in the list of allowed programs.
- Notify when Windows Firewall is blocking a new program.
I advise you to do it as shown in the picture.
In the block Public posting options put the switch on the field Turn on Windows Firewall.
After selecting all the necessary elements, click OK.

To learn all about firewall settings, you need to understand its purpose and purpose. Let's try to define the concepts of "firewall" and "firewall", whether they have any differences and similarities. Let's figure out network access and server configuration.
What's this?
Before doing short review on the firewall, you need to find out what is firewall... This is a conditional program that refers to computer network... It works with network traffic control and filtering. For this, there is a certain set of rules in the hardware and software part.
This is what the firewall is. firewall... WITH German language the word is translated as "fire wall". Often, users cannot tell the difference between a firewall and a firewall. This is not surprising, since both the first and the second are firewalls. The only difference is that firewall is a German term and firewall is English.
Windows version
Starting with Windows XP, the developer has implemented a firewall into the operating system. This is how the firewall settings became available. This does not mean that there was no such program element before. Previously released Internet version Connection Firewall. But the main advantage of the novelty was the presence of control over the access of programs to the network.
Danger
The old firewall entered computer system but was disabled by default due to compatibility errors. The settings of this firewall were available in the network configurations, which means that they became difficult to reach for some users. Since 2003, there have been a number of computer worm attacks. This was due to a system vulnerability.

In 2004, attacks continued, leading to lightning-fast infections of the system. To fix this, it was necessary to modify the firewall. This is how Windows Firewall became popular.
New
A security log was built into the new firewall, which collected data on IP addresses and connections over home, business, and the Internet. This service has hardly been updated since its release. Therefore, all settings of any parameters are suitable as for the old ones. operating systems and for new versions.
You can now configure the firewall in the Security Center because this firewall is part of it.
Enable / Disable
To configure firewall access settings, you need to understand how to enable or disable it. Of course, it is not recommended to disable it, as it would jeopardize the security of the system. But sometimes the shutdown is necessary in order to activate the antivirus program.

Most of these programs have a built-in firewall. To avoid compatibility conflicts, disable the built-in firewall. If the downloaded antivirus program does not have a firewall, then the version from Windows can be left.
To start working with this hardware and software element of the Network, you need to open it. As usual, there are several ways. You can simply enter its name into the search bar of the system. You will have a list of several options. Better to choose Windows Firewall.
Another option for approaching this service is going through the "Control Panel". To do this, you need to click "Start", find "Control Panel" in the right column, a window will open. Look at the right top corner, where there is a line "View" and select "Large icons" there. You will see a list in which you will find the proprietary firewall.
A new window will open where you can configure the firewall settings. In the left column there will be a line "Disable or enable firewall". There is a choice for home network and public. It's easy to turn off app lock notifications right there. It is imperative to check the box so that the program immediately notifies you about the malicious utility.
Blocking access
Some of the problems with accessing the Network are related specifically to the firewall. Perhaps you did not understand the work of the antivirus program and denied access to the network. You can restore it in the firewall settings. Again in the left column, go to the line "allow the launch of a program or component through a firewall."

A new window will open in front of you. It will contain a list of programs that are blocked or open access to the Network. You just need to check the boxes where necessary. For example, here you can find a browser that does not go to sites and give it permission to do so.
If you need to allow access to the Network in the firewall settings for a program that is not on the list, it is not difficult to do this. It is enough to find the button "Allow another program" under the sign containing the utilities. Then there will be additional list applications from which you can add another browser or software that needs access to the Web.
Remember that the more such permitted programs in the firewall, the less secure your work becomes. Ports that are opened are no longer monitored by the system and can be missed by malicious utilities.
Extended
To have more options for customizing access, you can use additional options. In this line, you can adjust the network profiles. Three options are used by default:
- Domain Profile is an option for PCs connected to a domain.
- Private - needed as a "bridge" to private network, it could be like home connection and working.
- Public - needed to connect to the public network.
Here you can also work with rules for different types of connections. Perhaps you need to configure the server. The firewall works easily with inbound or outbound connections. To do this, in the additional parameters, select the desired item and click on it by selecting "Create rule".

A special window will open with several steps. In each, everything is described in detail. There are several types of rules. If a rule for a program is used, then it is possible to configure the access of certain software to the Network. If it is for a port, then it is allowed or denied for it, a number of ports or a protocol.
You can also select a predefined or custom rule. Further, the setting is more than self-explanatory. Specify the path to the program, choose public or private access. You can also configure the permission or prohibition for a specific type of networks. Give a name to your profile and this completes the setup.
If you need more fine tuning, for example, prohibiting all software from connecting to a designated "ip" or port, or creating a list of "white" addresses, select custom rules.
If the Internet does not work, and there is no way to call a specialist urgently, you can try to adjust the settings yourself using our article.
Tip: before looking for solutions to problems in the network and router settings, check the status of your account with the provider and the reliability of the network cable, in about half of the cases this solves the problem.
Firewall or Antivirus?
Sometimes, Internet access can be blocked by the system's own protection agents, such as a firewall or antivirus. Determining the prohibition of the Windows 8 firewall is quite simple - disable it in the system settings and check the connection, if the network appears, the problem has been detected.
If the prohibition comes from the antivirus, you need to disable the program directly or terminate the corresponding processes through the task manager.
Configuring Windows Firewall
The main function of a firewall is to check data coming from the Internet and block those of concern. There are two modes "white" and "black" list. White - block everything except what is allowed, black - allow everything except what is prohibited. Even after full customization the firewall still needs to set permissions for new applications.
To find a firewall:

If you already have antivirus installed, disable the firewall as shown in this picture.
Blocking outgoing connections
Firewall and sometimes antivirus can completely block all outgoing connections.
To block outgoing connections with a firewall in white filter mode, you need to:
- go to the "advanced options" of the firewall;
- open the "Properties" window;
- put "outgoing connections" in "block" mode in the private and public profile.
Application rules
There is a special list of programs that are allowed to exchange data with the Internet and if the one you need is blocked, you just need to configure the permissions for it in this list. In addition, you can configure notifications so that if a new application is blocked, you have a choice - to leave everything as it is and allow access to this program.
For example, you can block access to the Internet for Skype or Google Chrome, or vice versa, leave access only for a couple of specific work programs.
Video: Networking without Internet Access
Service rules
To configure access for services:
- go to the advanced firewall settings;
- on the left, select incoming or outgoing rules;
- on the right, select the item "Create rule";
- select "Custom" in the list;
- enter the name of the service or select it from the proposed list.
In new Windows versions Starting with Vista, it is possible to select a service from the list without manually entering the service name. If there is no access to a computer in windows network xp or windows server, you need to configure the access policy service, then detailed description can be found in the system help.
Activating the reserved rule
To activate a reserved rule, you need to repeat steps 1-3 from the previous section, then:

Allow VPN connection
To set a special permission VPN connections, you need to repeat steps 1-3 again, then:

Configuring antivirus
If problems arise, one of the best options is to go to the antivirus website or contact technical support for the product, they will tell you exactly correct settings programs.
Antivirus should not block working programs - like google chrome or skype, but it should check them while running.
Safe antivirus settings should include:

Update
Antivirus updates must be up-to-date, either with the release of new versions, or automatically monthly.
No network access in Windows 7
If you see “ Unidentified network”, But all settings are in order, contact your provider first - it may be an internal error.
After reinstall Windows Internet settings usually return to the original ones, so you need to install them again:

Errors can cause the problem Windows protocol to fix this, you need to reset the protocol settings.
It's pretty simple:
- to run command line with administrator rights;
- enter and activate the command netsh int ip reset resetlog.txt;
- restart the laptop.
Is there a problem with your router or your laptop?
When you have problems connecting over WiFi, you need to determine what is the source of the problem. This could be a laptop, router, or ISP. If all devices connect to the router and work normally with the Internet - the reason is in the laptop, if on the contrary, connect network cable to the laptop and the Internet will work - you need to do the router settings. When all else fails, contact the technical support of the provider.

The reason is in the laptop
If the problem is in the laptop, but all of the above settings are in order, diagnose the system for viruses and device operation. Possible malfunctions network driver or even disruptions to work directly network card, connector.
Possibly does not match WiFi password dots, for example, due to incorrect layout or CapsLock.
The reason is the Wi-Fi router
Router at wrong settings can share WiFi without network access. How to properly configure the router - read on.
One of the reasons for connecting without a network can be to protect the Wi-Fi network from unauthorized access by blocking by MAC address. You can find out how to fix this problem on the router manufacturer's website, or independently find a list of allowed or denied addresses in the settings and add / delete the address of your laptop.
You can view the MAC address of your laptop by entering the Ipconfig / all command at the command line.
Also, the router has speed limit settings for each client, so you can both allow the speed to the maximum, and limit it to a couple of kbsecs.

Problems with the Internet speed can be a signal for help from the router itself - perhaps you did not remove the factory film from it, it is covered with something or overheats for other reasons. If the device is not provided with adequate ventilation, then it will not live long and is extremely ineffective.
Checking the Internet connection without a router
If you suspect a router of the problems that have arisen, you need to connect a network cable to your laptop or computer to check. If the Internet does not work automatically, create a new one cable connection, enter the login and password provided by the provider. You may need to enter additional settings protocols in adapter properties.
Internet connection setup
To check if the IPv4 settings of the computer correspond to the declared provider, you need to do the following:

- check the IPv4 address and gateway, they must match those provided by the provider during registration.
Setting up a connection through a router occurs through the device's web interface. Sometimes the router comes with a settings disc, but you can do without it. For initial setup It is best to connect the router directly to the laptop, and then to the Internet cable, connecting to the mains is done last.

If you do not have enough time to wait for a specialist, you do not want to spend money, you feel like a confident PC user, then using various instructions and recommendations, you can try to set up an Internet connection yourself. Most likely, it will take two to three times more time and energy than contacting a master, but it will provide useful experience in the future.
>
